I declare no conflict of interest. I’m just a happy user of Bitwarden and Authy (they’re free anyway).
- Problem 1: You Need Good Passwords
- Problem 2: Good Passwords Are Hard To Remember
- The Solution
- Can’t I Just Use My Browser?
- Overview of Bitwarden’s Security Protocol
- Two-Factor Authentication
- Conclusion
Problem 1: You Need Good Passwords
The bare minimum a website like Gmail does to keep your password secure in its database is to encrypt your password using a one-way pseudorandom function (input: plaintext password; output: pseudorandom hash i.e. long string of gibberish), so Google only have to see that the hash of the password you typed in matches the hash of your password stored on its database.
In the event of a data breach, the hacker can’t reverse the hash to get your password because of its pseudorandomness, but they can try all the combinations, though brute-force attacks start getting infeasible when your password is longer than 8 characters.
Instead, the hacker can pass a dictionary of the most common passwords like “password”, “qwerty”, and “12345678” through the same one-way pseudorandom function, and if any of the hashes match the leaked hash, they know they’ve cracked your password.
And such a dictionary attack is scarily easy to do.
Let’s say the hacker has a Nvidia Titan X graphics card (GPUs are only getting better), they can perform a dictionary attack with hashcat at the rate of 10 billion passwords per second using the cryptographically broken but still widely used 128-bit hash function MD5. If a better hash function is used, it will simply lower the rate to millions or thousands of passwords per second. Data breaches happen all the time, so the hacker can crack your password even faster by trying billions of real passwords.
Worse, Google, Facebook, Instagram, Twitter, GitHub all stored millions of passwords in plaintext! If even tech giants fail to do the bare minimum of encrypting all of their users’ passwords, what makes you think you can rely on smaller companies to secure your passwords?
Problem 2: Good Passwords Are Hard To Remember
The key idea in password strength is entropy i.e. the information held in a password. For example, a password made of 42 random bits has an entropy of 42 bits, which requires 242 (4,398,046,511,104) attempts to exhaust all possibilities during a brute-force search. Thus, increasing the entropy of the password by one bit doubles the number of guesses required.
To simplify, the general rules in choosing a password with high entropy are:
- Minimum password length of 8
- Generate passwords randomly
- Avoid character repetition, keyboard patterns, dictionary words, letter or number sequences
- Avoid using information that is or might become publicly associated with you, e.g. username, ID number, dates, or names of ancestors, romantic partners, relatives or pets
This means the better your passwords, the harder they are to remember.
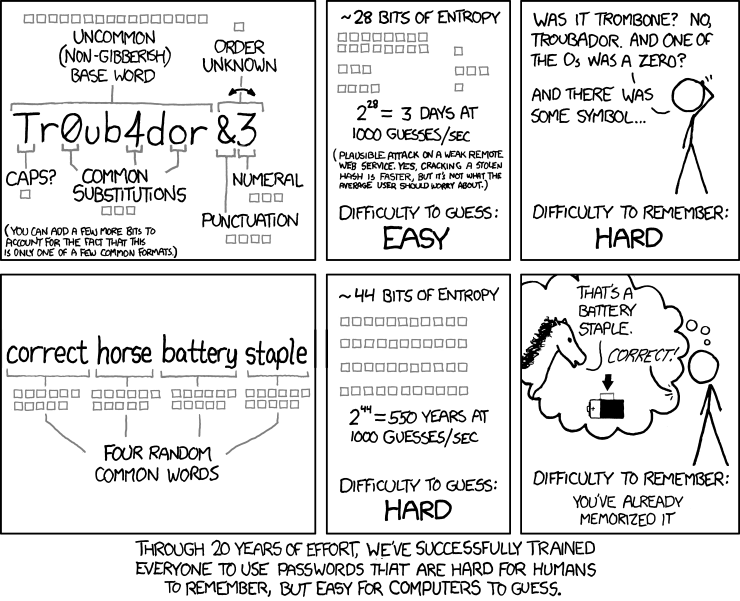
You have two options: write them down on a piece of paper, or use the same password.
The former is not a good solution because you may lose the piece of paper, it takes effort to come up with a unique, long, random password, and it’s inconvenient because you’ll have to look up your password every time you log in.
The latter is a terrible idea because no matter how strong that one password is, the hacker only needs to crack it once to gain access to all of your accounts.
The Solution
Enter password manager – encrypted list of all your passwords. You only need to memorise one strong master password to access your vault of strong passwords.
Putting all your eggs in one basket seems like a bad idea, so here is how password managers in general work, using Bitwarden’s simplified security protocol as an example:
- Passwords in the vault are encrypted using 256-bit AES-CBC (used by the US NSA for top secret information).
- Encryption key derived from master password using PBKDF2 SHA-256.
- You enter a strong master password
- On client side:
- Appends your master password with your email address
- Salts (adding a series of characters to) your master password using your email address
- hash (“password” + “ email”)
- After 100,001 iterations, the 256-bit hashed password is sent to the server
- On server side:
- Salts hash with a pseudorandom series of characters
- hash (“hashed password from client side” + “salt”)
- After another 100,000 iterations, the 256-bit hash is stored on the server as the encryption key
- When authenticating with the server (Microsoft Azure Cloud US or self-hosted), a copy of the encrypted vault is downloaded on your device.
- When you access the vault, it is decrypted using your encryption key and stored in RAM only
- When the vault is locked, the data is purged from RAM
As the hash functions are one-way only, meaning no one could reverse-engineer them into your master password, they’re also virtually useless to hackers.
Can’t I Just Use My Browser?
Using your browser’s built-in password storage is better than nothing, but other than zero-knowledge security protocol, password managers have better features. Bitwarden again for example:
- Supports multiple operating systems (Windows, macOS, Linux, iOS, Android)
- Supports extension on multiple browsers to auto-fill usernames and passwords (Chrome, Firefox, Safari, Edge, Opera, Vivaldi, Brave, Tor)
- Supports web vault on any browser
- Generates customisable pseudorandom passwords or passphrases
- Vault timeout and biometric authentication
- Stores other data e.g. software product keys, addresses, bank accounts, and credit card numbers
- Identifies passwords and other data that have been compromised in data breaches, reused passwords, and weak passwords
- Logs or clears password history
- Identifies URIs that use unsecured schemes
- Supports sharing usernames and passwords
- Emergency access (grants one person access to your vault in case of emergency)
- Self-host option
Self-hosted password managers, encrypted Excel spreadsheets (any document before Office 2007 is insecure) or markdown files all are better than nothing, but you won’t be able to enjoy any of the features listed above, with the biggest cons being
- Possibly lower security
- No access from other devices (e.g. can’t login on your phone when you’re out)
- Having to manually lookup and type in password for every login
- Regular manual backups
- Cumbersome password sharing
The more friction it is to use, the less you’ll use it, so save yourself the hassle and enjoy the cloud-based password managers. There are plenty of good options; I use Bitwarden because it is free (with the most complete features and no limits), secure, cloud-based, open-source, audited by third-parties, and is consistently the top free recommendation.
Overview of Bitwarden’s Security Protocol
Feel free to skip to the next section if you’re not interested to know how it works in detail.
Some password managers have more sophisticated security protocols; below is from Bitwarden’s security whitepaper.
Upon account creation:
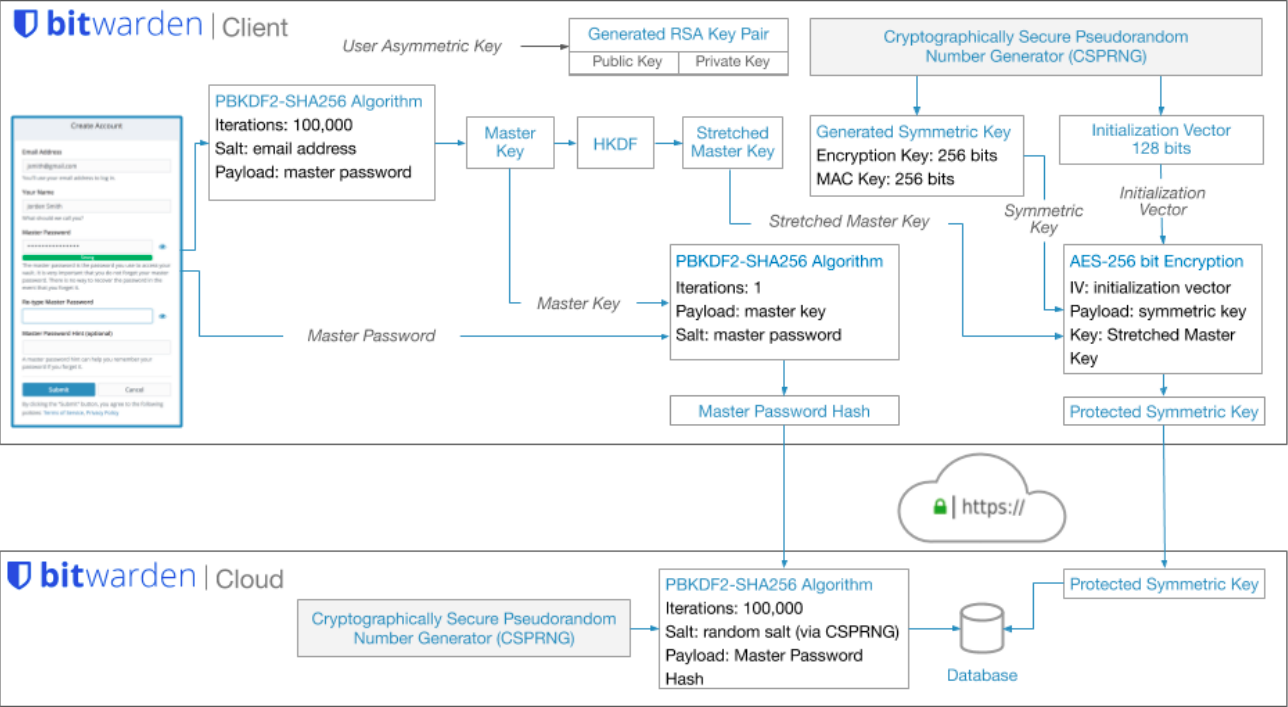
- On client side:
- Produce Master Password Hash and Stretched Master Key
- Salts your Master Password using your email address
- hash (“Master Password + “email address”) using PBKDF2 SHA-256 with 100,001 iterations to produce 256-bit Master Key
- hash (“Master Key”) using HKDF to produce 512-bit Stretched Master Key
- hash (“Master Password” + “Master Key”) using PBKDF2 SHA-256 with 1 iteration to produce 256-bit Master Password Hash
- Send Master Password Hash to server for authentication
- Produce Protected Symmetric Key
- Produce pseudorandom 512-bit Symmetric Key (same key for encryption of plaintext and decryption of ciphertext, as opposed to public/asymmetric keys i.e. pair of public and private keys
- Produce pseudorandom 128-bit Initialisation Vector (to randomise a set of input blocks before encryption)
- encrypt (“Initialisation Vector” + “Symmetric Key” + “Stretched Master Key”) using AES-CBC to produce 256-bit Protected Symmetry Key
- Send Protected Symmetry Key to server for authentication
- Purge all keys from RAM
- Produce Master Password Hash and Stretched Master Key
- On server side:
- hash (“Master Password Hash” + “pseudorandom salt”) using PBKDF2 SHA-256 with 100,000 iterations to produce 256-bit **hash of Master Password Hash **for storage
Upon login:
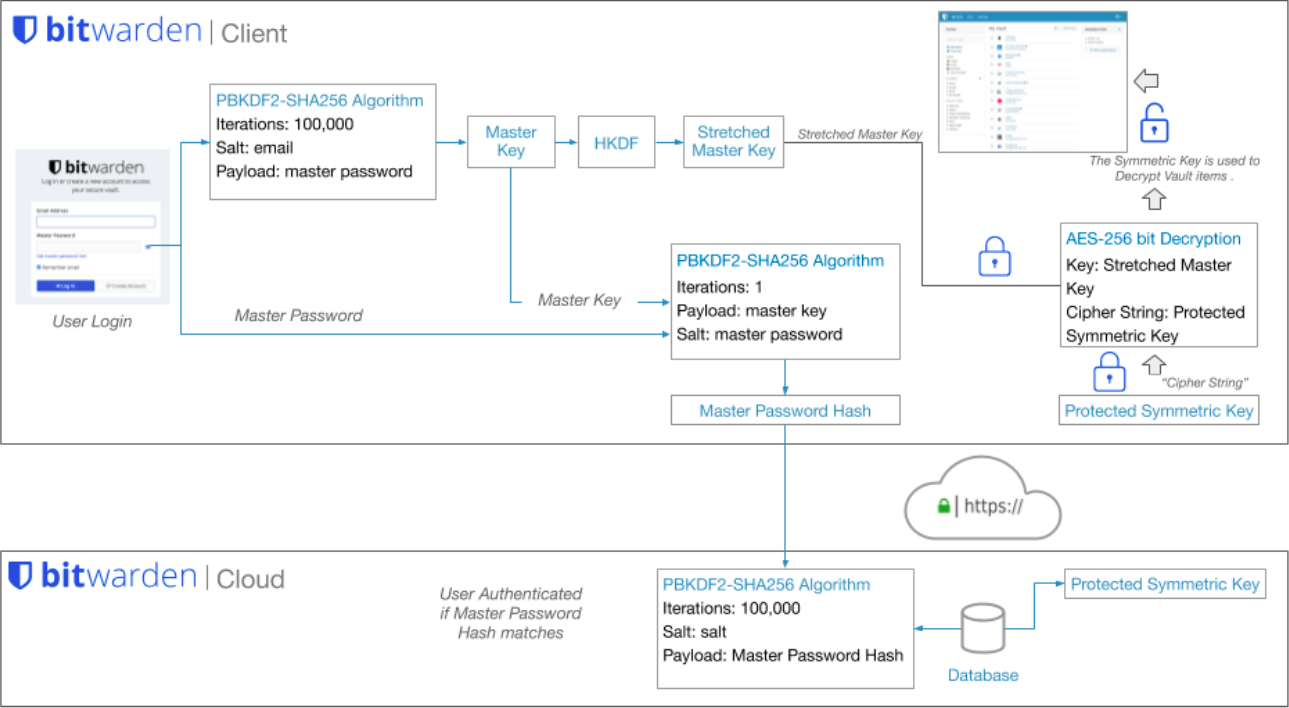
- On client side:
- Produce Master Password Hash and Stretched Master Key
- Salts your Master Password using your email address
- hash (“Master Password + “email address”) using PBKDF2 SHA-256 with 100,001 iterations to produce 256-bit Master Key
- hash (“Master Key”) using HKDF to produce 512-bit Stretched Master Key
- hash (“Master Password” + “Master Key”) using PBKDF2 SHA-256 with 1 iteration to produce 256-bit Master Password Hash
- Send Master Password Hash to server for authentication
- Produce Master Password Hash and Stretched Master Key
- On server side:
- hash (“Master Password Hash” + “pseudorandom salt”) using PBKDF2 SHA-256 with 100,000 iterations to produce 256-bit hash of Master Password Hash
- Authenticate your login if the **hash of Master Password Hash **produced upon login matches the stored **hash of Master Password Hash **produced upon account creation
- If authenticated, send Protected Symmetric Key produced upn account creation to client
- On client side:
- hash (“Master Key”) using HKDF to produce 512-bit Stretched Master Key
- decrypt (“Stretched Master Key” + “Protected Symmetric Key”) using AES-CBC to produce Symmetric Key
- decrypt vault items (e.g. username/password) using Symmetric Key
- Purge all keys from RAM when vault is locked or timeout
So your Master Password and Symmetric Key (the “encryption key”) are only stored in and purged from RAM, and never sent to Bitwarden servers.
The mid 2021 release of Admin Password Reset introduced a new RSA Public/Private Key Pair for all Organizations. The RSA Private Key is further encrypted with the Organizationʼs pre-existing symmetric key before being stored. The RSA-2048 (2,048-bit) Key Pair is generated and encrypted client-side upon creation of a new Organization.
Two-Factor Authentication
Even if your password manager is secure, and passwords strong, you’re still vulnerable to attacks like keylogging and phishing, or simply people looking over your shoulder. Two-factor authentication simply means a method additional to a password like a bankcard, your phone, or a key.
Of course, the most secure setup is a completely self-hosted offline password manager coupled with a hardware security token like FIDO2 USB security keys , but that comes with significant costs to convenience. 2FA using SMS is better than nothing but is insecure as it is plaintext that is easily tracked and intercepted due to telephone network protocol vulnerabilities, and is vulnerable to SIM swapping attacks.
The next best thing is authenticator apps like Authy, which is just as convenient as SMS but much more secure:
- Offline – 2FA tokens generated directly on device
- Protected with biometric, PIN, or password
- 2FA data encrypted without storing on their servers, only decrypted on phone RAM
- Optional secure cloud backup
- No lockouts if phone lost (unlike Google Authenticator)
- Supports multiple devices (iOS, Android, Chrome, Windows, macOS)
- Supports any site that uses TOTP (time-based one-time passcode) and Google Authenticator
Again there are multiple good options; I use Authy because it is free, most feature-rich, well supported by its parent company Twilio, best UI design, transparent, recommended by Bitwarden, and is one of the top recommendations in general.
Conclusion
It does take a bit of time to enter all your accounts (I had more than a hundred) into Bitwarden and Authy at the start, but you can make the migration easier by importing data into your vault.
Trust me: you’ll get so used to the sublime convenience of auto-fill username, password, and even card details; it brings me joy every time I use Bitwarden. They’re such low-hanging fruits that you’ll wonder why you waited until now to start using a password manager and an authenticator app.
